Information Security
Table of Content:
·
SQL
Injection Attacks
· SQL Injection Techniques
· SQLi
Attacks Avenues
· Malware
· Firewalls
· Software
Security
· Feistel
Cipher
· Feistel
Cipher for DES & 3DES
· Cipher
Block Modes -1
· Cipher
Block Modes -2
· SQL Injection Attacks (SQLi)
The
SQLi attack is one of the most prevalent and dangerous network-based security
threats.
OR
SQLi is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access.
What is the impact of a successful SQL injection attack?
A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information.
SQL Injection Examples:
There are a wide variety of SQL
injection vulnerabilities, attacks, and techniques, which arise in different
situations. Some common SQL injection examples include:
|
Retrieving hidden data |
where you can modify an SQL query to return additional results. |
|
Subverting application logic |
where you can change a query to interfere with the application's logic. |
|
UNION attacks |
where you can retrieve data from different database tables. |
|
Examining the database |
where you can extract information about the version and structure of the database. |
|
Blind SQL injection |
where the results of a query you control are not returned in the application's responses. |
The SQLi attack typically works by prematurely terminating a
text string and appending a new command. Because the inserted command may have
additional strings appended to it before it is executed, the attacker
terminates the injected string with a comment mark “--”. Subsequent text is ignored
at execution time.
· SQLi Attacks Avenues
We can characterize SQLi attacks in terms of the avenue of attack and the type of attack. The main avenues of attack are as follows:
· User input: In this case, attackers inject SQL commands by providing suitably crafted user input.
· Server variables: Server variables are a collection of variables that contain HTTP headers, network protocol headers, and environmental variables. Web applications use these server variables in a variety of ways, such as logging usage statistics and identifying browsing trends. If these variables are logged to a database without sanitization, this could create an SQL injection vulnerability.
· Second-order injection: Second-order injection occurs when incomplete prevention mechanisms against SQL injection attacks are in place.
· Cookies: When a client returns to a Web application, cookies can be used to restore the client’s state information. Because the client has control over cookies, an attacker could alter cookies such that when the application server builds an SQL query based on the cookie’s content, the structure and function of the query is modified.
Malware is the collective name for a number of malicious software variants, including viruses, ransomware and spyware. Shorthand for malicious software, malware typically consists of code developed by cyber-attackers, designed to cause extensive damage to data and systems or to gain unauthorized access to a network. Malware is typically delivered in the form of a link or file over email and requires the user to click on the link or open the file to execute the malware.
OR
Malware is any piece of software that is designed with the intent to damage, disrupt or gain unauthorized access to your device and inflict harm to data and/or people in multiple ways.
OR
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network (by contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug). A wide variety of malware types exist, including computer viruses, worms, Trojan horses, adware, Attack Kit, Auto-rooter, Backdoor and Zombie etc.
Types of Malwares:
Viruses
viruses attach their malicious code to clean code and wait for an
unsuspecting user or an automated process to execute them. They are usually
contained within an executable file.
Worms
Worms are spread via software vulnerabilities or phishing attacks. Once
a worm has installed itself into your computer’s memory, it starts to infect
the whole machine and, in some cases, your whole network.
Trojan Horses
A Trojan horse, or Trojan, is a type of malicious code or software that
looks legitimate (legal / Authentic) but can take control of your computer. A
Trojan is designed to damage, disrupt, steal, or in general inflict some other
harmful action on your data or network.
Adware
Adware is one of the better-known types of malware. It serves pop-ups
and display ads that often have no relevance to you.
Attack Kit
An exploit kit (Attack Kit) is a programming tool that allows someone who does not have any experience writing software code to create, customize and distribute malware. Exploit kits are known by a number of other names, including infection kit, crimeware kit, DIY attack kit and malware toolkit.
Exploit kits have graphical application program interfaces (APIs) that
allow non-technical users to manage sophisticated attacks capable of stealing
corporate and personal data, orchestrating denial of service (DoS) exploits or
building botnets.
Auto-Rooter
LevelDropper as auto-rooting malware, as it silently roots a device in order to gain system level privileges. This allows it to perform actions off-limits to most apps and to effectively take control of the infected device, bypassing many of Android's built-in security protections.
Backdoor
The backdoor attack is a type of malware that is used to get
unauthorized access to a website by the cybercriminals. The cybercriminals
spread the malware in the system through unsecured points of entry, such as
outdated plugins or input fields.
Zombie (BOT)
A bot is a computer that’s been infected with malware so it can be
controlled remotely by a hacker.
A Firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network.
Firewall Design Goals
1. Any traffic going outside the system and moving into the system must pass through the firewall.
2. Only local security policy authorized traffic will be able to get into and out of the firewall.
3. Internal threats are often at bay as the firewall provides alert of a possible malware threat.
· Types of Firewall
1. Packet Filtering
packet-filtering firewalls basically create a checkpoint at a traffic router or switch. The firewall performs a simple check of the data packets coming through the router—inspecting information such as the destination and origination IP address, packet type, port number, and other surface-level information without opening up the packet to inspect its contents.
2. Stateful
inspection firewalls
Stateful inspection functions like a packet
filter by allowing or denying connections based upon the same types of filtering.
However, a stateful firewall also monitors the “state” of a communication.
for example, when you connect to a Web server and
that Web server must respond to you, the stateful firewall has the proper
access open and ready for the responding connection. When the connection ends,
that opening is closed.
3. Application-level
gateways
Proxy firewalls operate at the application layer
to filter incoming traffic between your network and the traffic source—hence,
the name “application-level gateway.
What is difference between outbound TCP connections and inbound TCP connections?
If
the Windows Firewall is turned off then it will have no effect, and the Inbound
and Outbound rules will mean nothing.
Inbound rules: These are to do with other things accessing your
computer. If you are running a Web Server on your computer then you will have
to tell the Firewall that outsiders are allowed to connect to it.
Outbound rules: These are so that you can let some programs use
the Internet, and Block others. You will want to let your Web Browser (Internet
Explorer, Firefox, Safari, Chrome, Opera...) have access to the Internet, so
you will tell Windows Firewall that it's allowed.
Software security is an idea implemented to protect software against malicious attack and other hacker risks so that the software continues to function correctly under such potential risks. Security is necessary to provide integrity, authentication and availability.
Input Size & Buffer Overflow
Buffers are memory storage regions that temporarily hold data while it is being transferred from one location to another. A buffer overflow (or buffer overrun) occurs when the volume of data exceeds the storage capacity of the memory buffer.
For example, a buffer for log-in credentials may be designed to expect username and password inputs of 8 bytes, so if a transaction involves an input of 10 bytes (that is, 2 bytes more than expected), the program may write the excess data past the buffer boundary.
Interpretation of Program Input? (ye topic mjhy clear ni hy is liye ni likha khud dekhna chahen to slide # 18 par dekh len)
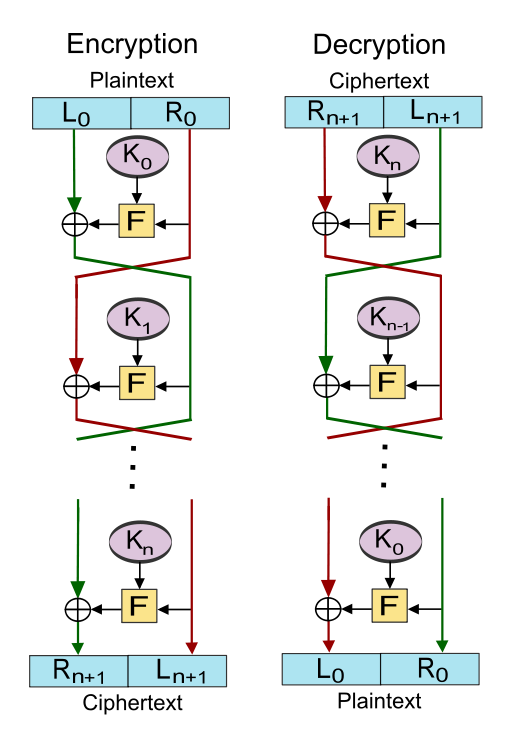
· Feistel Cipher
A Feistel network uses a round function, a function which takes two inputs, a data block and a subkey, and returns one output the same size as the data block. In each round, the round function is run on half of the data to be encrypted and its output is XORed with the other half of the data. This is repeated a fixed number of times, and the final output is the encrypted data.
Example:
Let F be the round function and let K0,K1,....,Kn be the sub-keys for the rounds 0,1,....,n respectively.
Then the basic operation is as follows:
Split the plaintext block into two equal pieces, (L0, R0)
For each round i = 0,1,....,n, compute.
Li+1
= Ri
Ri+1 = Li ⊕ F(Ri, Ki).
Where ⊕ means XOR. Then the ciphertext is (Rn+1,
Ln+1).
Decryption of a (Rn+1, Ln+1) is accomplished by computing for i = n, n-1, ...., 0.
Ri
= Li+1
Li = Ri+1
⊕ F(Li+1, Ki).
Then (L0, R0) is the plaintext again.
The diagram illustrates both encryption and decryption. Note the reversal of the subkey order for decryption; this is the only difference between encryption and decryption.
·
Feistel
Cipher for DES & 3DES
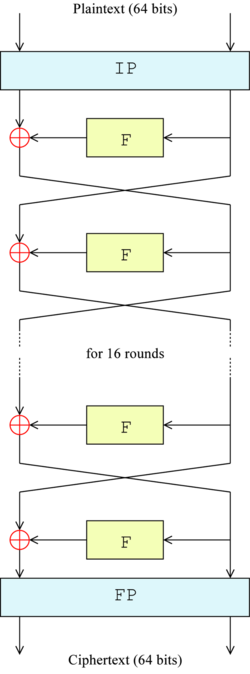
Data Encryption Standard (DES)
The most widely used encryption scheme is based on the Data Encryption Standard, (DES) adopted in 1977 by the National Bureau of Standards.
The DES algorithm can be described as follows:
The plaintext is 64 bits in length and the key is 56 bits in length; longer plaintext amounts are processed in 64-bit blocks. The DES structure is a minor variation of the Feistel network. There are 16 rounds of processing. From the original 56-bit key, 16 subkeys are generated, one of which is used for each round. The process of decryption with DES is essentially the same as the encryption process.
The rule is as follows:
Use the ciphertext as input to the DES algorithm, but use the subkeys Ki in reverse order. That is, use K16 on the first iteration, K15 on the second iteration, and so on until K1 is used on the sixteenth and last iteration.
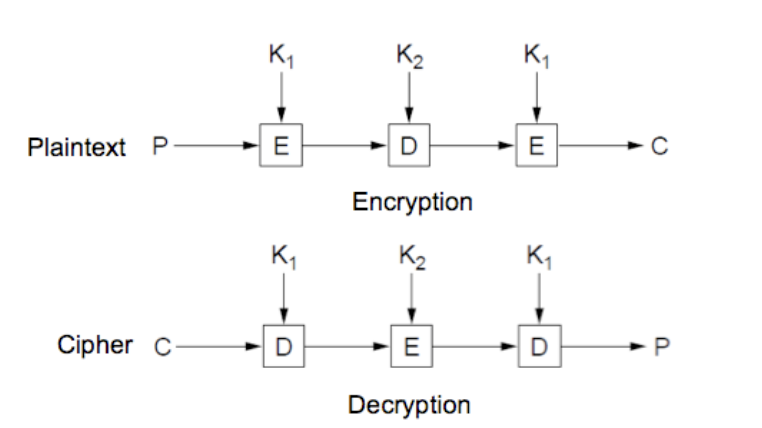
3 Data Encryption Standard (3DES)
3DES uses three keys and three executions of the DES algorithm. The function follows an encrypt-decrypt-encrypt (EDE) sequence.
C = E(K3, D(K2, E(K1, p)))
Where,
C = ciphertext
P = plaintext
E[K, X] = encryption of X using key K
D[K, Y] = decryption of Y using key K
Decryption is simply the same operation with the keys reversed.
P = D(K1, E(K2, D(K3, C)))
There is no cryptographic significance to the use of decryption for the second stage of 3DES encryption. Its only advantage is that it allows users of 3DES to decrypt data encrypted by users of the older single DES:
C = E(K1, D(K1, E(K1, P))) = E[K, P].
·
Cipher
Block Modes -1
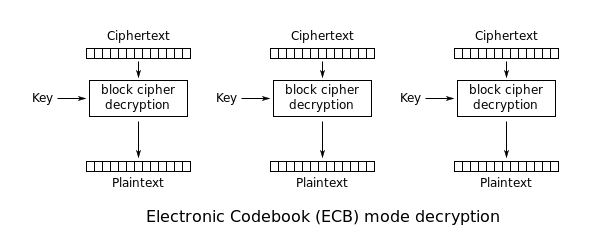
Mode Name: Electronic Code book (ECB).
Description: Each block of 64 plaintext bits is encoded independently using the same key.
Application: Secure transmission of single values (e.g., an encryption key).
Deep Brief
This mode is a most straightforward way of processing a series of sequentially listed message blocks.
Operation
· The user takes the first block of plaintext and encrypts it with the key to produce the first block of ciphertext.
· He then takes the second block of plaintext and follows the same process with same key and so on so forth.
The ECB mode is deterministic, that is, if plaintext block P1, P2,..., Pm are encrypted twice under the same key, the output ciphertext blocks will be the same.
·
Cipher
Block Modes -2
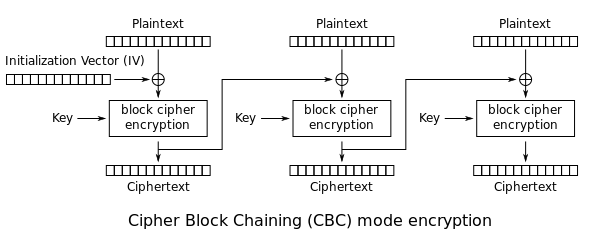
Mode Name:Cipher Block Chaining (CBC).
Description:The input to the encryption algorithm is the XOR of the next 64 bits of plaintext and the preceding 64 bits
of ciphertext.
Application:General-purpose block-oriented transmission|Authentication.
Deep Brief
CBC mode of operation provides message dependence for generating ciphertext and makes the system non-deterministic.
Operation
The operation of CBC mode is depicted in the following illustration. The steps are as follows −
· Load the n-bit Initialization Vector (IV) in the top register.
· XOR the n-bit plaintext block with data value in top register.
· Encrypt the result of XOR operation with underlying block cipher with key K.
· Feed ciphertext block into top register and continue the operation till all plaintext blocks are processed.
· For decryption, IV data is XORed with first ciphertext block decrypted. The first ciphertext block is also fed into to register replacing IV for decrypting next ciphertext block.
In CBC mode, the current plaintext block is added to the previous ciphertext block, and then the result is encrypted with the key. Decryption is thus the reverse process, which involves decrypting the current ciphertext and then adding the previous ciphertext block to the result.
Advantage of CBC over ECB is that changing IV results in
different ciphertext for identical message.
Drawback: the error in transmission gets propagated to few further blocks during decryption due to chaining effect.
Learn more modes operations from given below book [page #655]
[I'm not responsible for anything!]
Don’t just relay on this document, you can learn more as much as you want from given book. [download here]
Thenanosoft.com | Farhan Ellahi